A Typical Distributed Denial of Service Attack
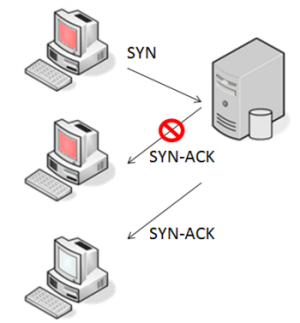
A SYN flood DDoS attack occurs when several zombies send multiple, rapidly repeated TCP SYN requests to the targeted server but do not acknowledge the SYN transmission. If the zombies never acknowledge the SYN request, the server will keep open the connection until a time-out occurs. However, this form of attack has the distinct disadvantage of identifying the zombie via its source IP address.
A better form of attack would be to spoof the IP address of an "innocent" end node, causing the targeted server to send a SYN-ACK to these spoofed addresses. The nodes that now receive the SYN-ACK from the server are either not in the SYN_SENT state or in that state with a different destination IP address. In either case, the innocent nodes will disregard the SYN-ACK and will not respond to the targeted server. Thus the targeted server will keep the connection open until the timeout expires — waiting for an ACK that will never come. These half-open connections consume resources on the targeted server. If enough of these connections are established, the server's resources could be exhausted, thereby blocking additional connections from occurring.
The attack can be further enhanced by generating random IP addresses, avoiding the suspicious behavior of an innocent node repeatedly requesting a large number of connections.
Zombie device is depicted with a red screen.